Ty Nixon
Ty Nixon
Senior Network Engineer
Have you been compromised by ransomware? Has your network been breached by uncontrolled wired or wireless access? By now, most IT professionals are familiar with the basic concepts of network access control. Several vendor partners offer robust solutions for this security need. As is the case for most security needs, the demand for strict access control measures continues to grow exponentially across all verticals. Numerous companies, ranging from local to global, have found themselves to be victims of malicious attacks originating from inadequate network access controls. Simply put, many organizations have little or no way to detect and prevent malicious attacks from guests and patrons physically connecting to internal networks providing access to sensitive data.
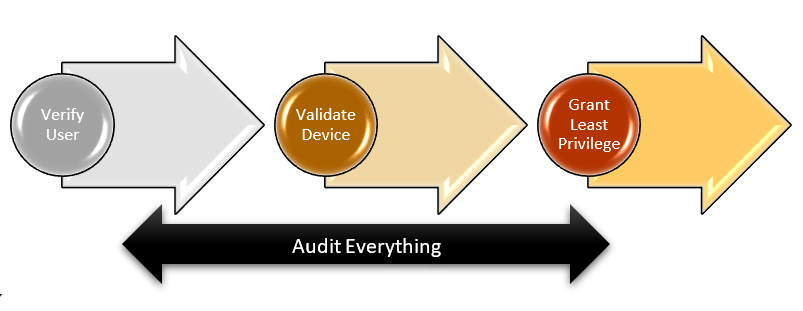 With modern Identity-Based Networking Solutions, multiple factors are considered as part of the Authentication and Authorization decisions. Additionally, robust alerting and reporting are available as a result of the Accounting process. As with most security technologies, such a solution should be viewed as a piece of the overall security puzzle. Network access control should be included as a foundational layer in any security stack.
With modern Identity-Based Networking Solutions, multiple factors are considered as part of the Authentication and Authorization decisions. Additionally, robust alerting and reporting are available as a result of the Accounting process. As with most security technologies, such a solution should be viewed as a piece of the overall security puzzle. Network access control should be included as a foundational layer in any security stack.
Keller Schroeder’s qualified network security professionals have successfully guided dozens of clients through the planning and implementation phases, as well as through the long-term support of such solutions. Our comprehensive offering can aid your business during the scoping process, equipment implementation timeline, and support throughout the lifecycle of the solution. Our solutions can be simple enough to scale down to the smallest of environments, yet robust enough to accommodate the largest of enterprises.
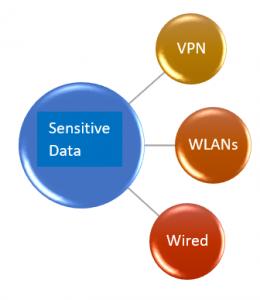
Common Entry Points for Network-Based Attacks:
- VPN and Remote Access Services
- Wireless SSID Misuse
- Wired Network Drop Manipulation
- Compromised Network Device Administration
- Network Endpoint Theft and Misuse
- Social Engineering
Common Solutions for Mitigating Network-Based Attacks:
- 1X and MAC Authentication Bypass
- Centralized Web Authentication
- Traditional Network Segmentation
- Microsegmentation
- Network Virtualization
- Multifactor Authentication
- Posturing, Quarantining, and Remediation
Keller Schroeder would love to discuss zero-trust network access and the opportunity to assist in adding value to your infrastructure security purchase. Our team of experienced and certified engineers is eager to assist you on your journey to Zero-Trust Network Access Control. To learn more, reach out to your Keller Schroeder Select Account Manager.